diff options
| -rw-r--r-- | _posts/2021-05-14-intercepting-golang-tls-with-wireshark.md | 10 |
1 files changed, 5 insertions, 5 deletions
diff --git a/_posts/2021-05-14-intercepting-golang-tls-with-wireshark.md b/_posts/2021-05-14-intercepting-golang-tls-with-wireshark.md index ee86fe9..4b51c15 100644 --- a/_posts/2021-05-14-intercepting-golang-tls-with-wireshark.md +++ b/_posts/2021-05-14-intercepting-golang-tls-with-wireshark.md @@ -7,13 +7,13 @@ services][mitmproxy-post]. This is a continued exploration of debugging network services, in particular focused around inspecting TLS encrypted traffic that your application is sending and receiving. -Transport Layer Security is a fundamental building block of secure -communications on the Internet today, and increasingly the software we write is +Transport Layer Security is a fundamental building block of modern secure +communications on the Internet, and increasingly the software we write is expected to be a fluent speaker of TLS. While this brings security benefits for users, it also increases the complexity of understanding what our software is doing because when we try to use tools like Wireshark or tcpdump to inspect network traffic, all we see is encrypted data. Let's see what a regular HTTP -request looks like in Wireshark: +request looks like in Wireshark: ``` $ curl http://www.benburwell.com @@ -22,8 +22,8 @@ $ curl http://www.benburwell.com 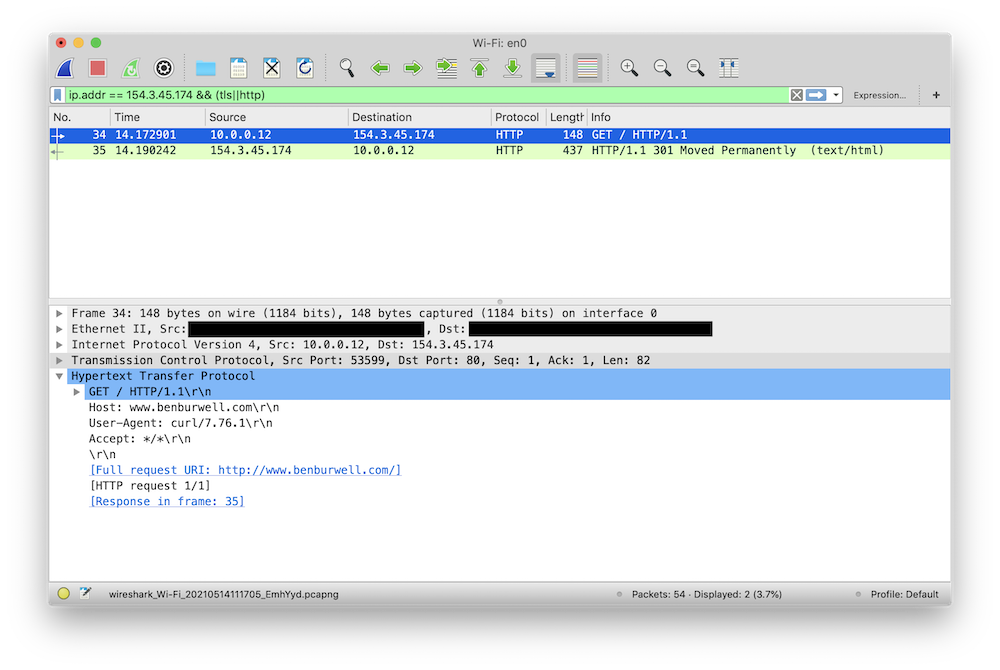 -Here, we can see the HTTP request and response. But what happens when we make -the request over TLS? +Here, we can see the HTTP request and response. But what happens when we make +the request over TLS? ``` $ curl https://www.benburwell.com |
